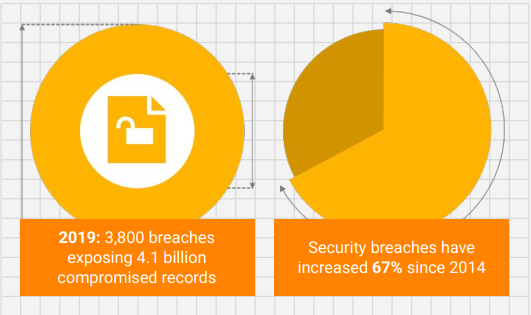
According to Forbes, In the first half of 2019 alone, there were 3,800 publicly disclosed breaches exposing 4.1 billion compromised records. According to Accenture, security breaches have increased 67% since 2014, and we only expect those numbers to increase.
Couple that with an always-on user-base that is constantly switching devices, how do you ensure that your business and your end-user data is safe?
YOUR END-USERS LOG IN EVERYWHERE FROM EVERY DEVICE
Gone are the days when your end-users (customers and employees)
accessed their accounts from only one place on only one device. Today,
users need flexibility as they work from home, access your app from their
device while sitting on a beach sipping a Mai Tai, or start a project on their
phone but complete it on their laptop.
Without an Identity and Access Management solution to centralize logins
and activity, you are opening your organization up to considerable risk from
a lack of governance around remote access and managing credentials.
PEOPLE OFTEN HAVE BAD PASSWORD HABITS
Today, passwords remain the main tool for verifying a user’s identity. But
the bottom line is that end-users rarely have good password practices. Who
has time to develop a new, secure password for every single application
that you sign up for? Instead, most people reuse passwords, use
easy-to-guess passwords, or write their passwords down on a sticky note.
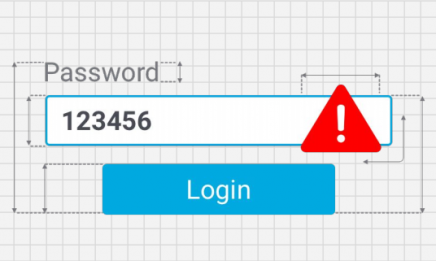
In fact, according to a CNN report, “123456” is the number one most
common password. And with passwords like that, you are leaving yourself
open to even the least sophisticated hackers.
SAAS ADOPTION IS EXPLODING
AS YOUR BUSINESS MOVES TO
THE CLOUD
With the move to the cloud, SaaS applications are more accessible and
easier to procure than ever before. Plus, these applications are now
often purchased outside of central IT as software gets easier for
line-of-business stakeholders to implement and adopt. And without a
centralized hub to manage your apps, you have SaaS sprawl with
inconsistent policies for security and access.